Default Networking Setup
When you create a project in evroc, a complete networking environment is automatically configured for you. This default setup includes all the essential components needed to deploy VMs with both internal and external connectivity.
What gets created automatically
Each new project includes:
- Virtual Private Cloud (VPC) - An isolated network environment for your resources, spanning all zones in the region
- Subnets - One subnet per zone, each with its own private IP address range for VM-to-VM communication
- Default Security Groups - Firewall rules controlling network traffic to and from VMs
These resources are created automatically and can't be deleted separately from the project.
How the components work together
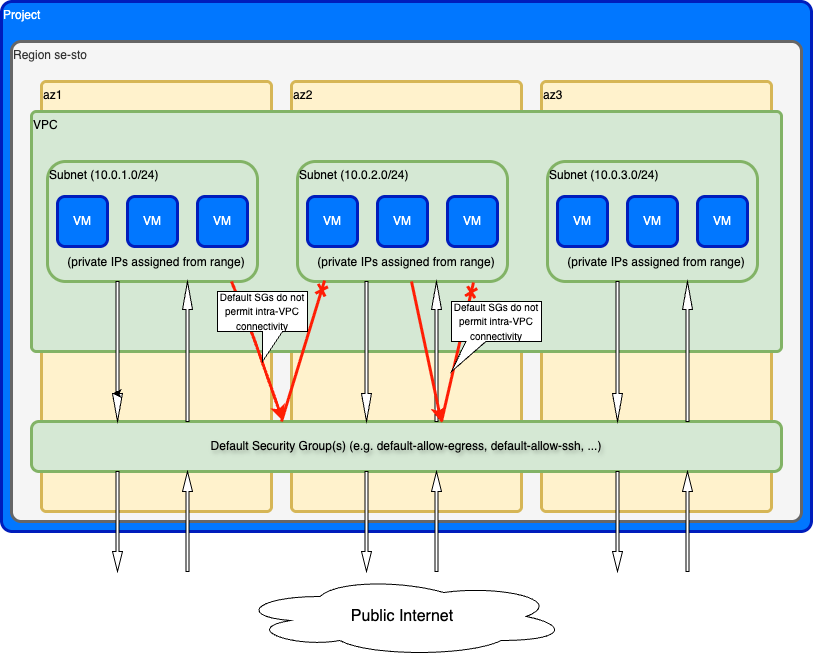
VPC and subnets
The VPC provides network isolation for your resources and spans all availability zones in the region. Each zone has its own subnet with a dedicated IP address range:
| Zone | Subnet | CIDR |
|---|---|---|
| se-sto-a | default-se-sto-a | 10.0.1.0/24 |
| se-sto-b | default-se-sto-b | 10.0.2.0/24 |
| se-sto-c | default-se-sto-c | 10.0.3.0/24 |
Each subnet provides 252 usable private IP addresses. When you create a VM, it is assigned a private IP from the subnet in its zone.
VMs in different zones can communicate with each other over the VPC's private network, subject to security group rules.
Internet connectivity
VMs can connect to the internet as follows:
- Outbound traffic: Enabled by default for all VMs (if security groups allow). Traffic uses a shared IP address unless you attach a Public IP to the VM
- Inbound traffic: Requires you to attach a Public IP to the VM and configure appropriate security group rules
Default security groups
All projects include three preconfigured security groups:
default-allow-egress (automatically applied to VMs if no other security groups are specified):
- Allows all outbound traffic from VMs to the internet
- Blocks all inbound traffic from external sources
VMs are automatically added to this security group unless you specify different security groups when creating the VM. This group doesn't allow VMs to communicate with each other.
default-allow-web-protocols (must be explicitly applied):
- Allows HTTP traffic (TCP port 80) from any IP address
- Allows HTTPS traffic (TCP port 443) from any IP address
Add VMs to this group if they serve web traffic and need to accept HTTP/HTTPS connections from the internet. This group doesn't allow general inter-VM communication.
default-allow-ssh (must be explicitly applied):
- Allows SSH access (port 22) from any IP address (0.0.0.0/0)
- Must be explicitly added to VMs that need SSH access from the internet
This security group provides a convenient way to enable SSH access without creating custom rules. You can add it when creating a VM or update an existing VM to include it.
What you need to configure
While the basic networking is set up automatically, you'll need to configure:
- Public IPs - Create and attach these to VMs that need inbound internet access
- Custom Security Groups - Define firewall rules for traffic control, including inter-VM communication
- SSH Keys - Configure SSH access to your VMs
If your VMs need to communicate with each other within the VPC - including within the same subnet - create a custom security group with rules that allow the required traffic between them.
Next steps
- Learn about Regions and zones and how resources are distributed
- Learn about Virtual Private Clouds (VPCs)
- Learn about Subnets
- Configure Security Groups for custom firewall rules
- Learn how to create VMs
- Learn how to view VPCs and subnets